As the threat landscape continues to evolve, organisations must stay vigilant and proactive in their cyber security efforts to protect themselves and their stakeholders from the detrimental impact of cyber attacks.
Staying cyber-aware is your best line of defence.
Our range of penetration testing and cyber security services proactively mitigate the risk of breaches, helping to keep your business-critical applications and data protected.
Be assured, be secured with Pentiq.
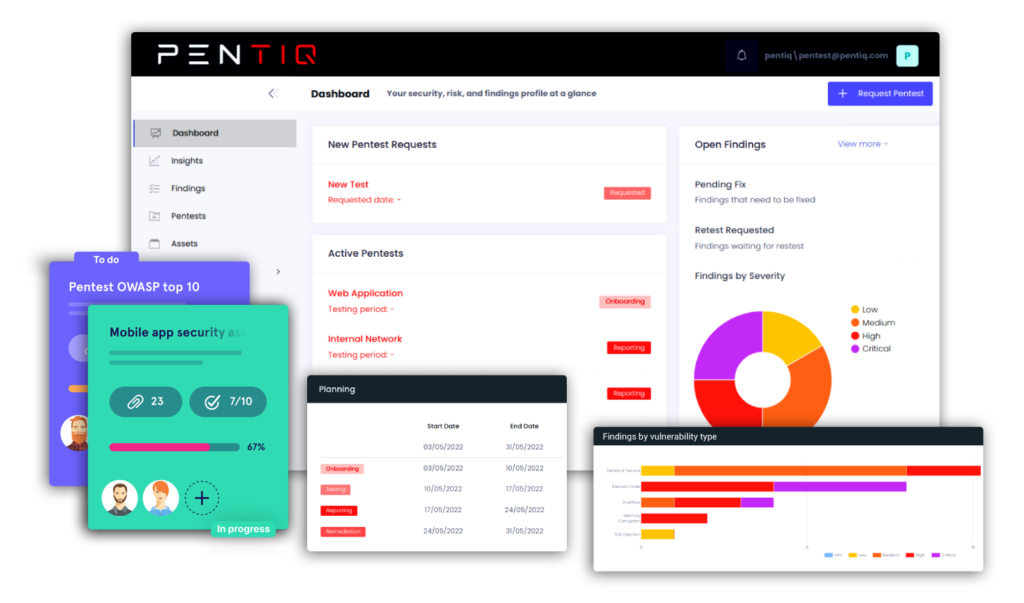
Our CREST-certified experts specialise in penetration testing, training, compliance and consulting to help increase your security posture and business agility.
This type of test assesses the security of your web and mobile applications to ensure they’re configured correctly and free from vulnerabilities. We’ll work to find improvement areas and provide strategic insights on how best to remediate any weaknesses found.
Our team of experts measures the level of internal risk your organisation faces by looking at the configuration of your network, devices or system from the viewpoint of a user with authorised access to your internal infrastructure.
Our external penetration testing service checks external-facing systems like web servers, firewalls, and network devices to identify vulnerabilities. Testers get the same level of access as an external hacker, so you get a real risk indicator of your external security posture.
Cloud penetration testing involves a combination of manual and automated testing techniques to identify potential vulnerabilities in your cloud infrastructure, virtual machines, web applications, databases and other services hosted on the cloud.
Check the quality and security of an application’s source code early in SDLC to help reduce the cost and complexity of remediation later on. We look for potential vulnerabilities, such as SQL injection, cross-site scripting (XSS), buffer overflows and other issues.
From breach and attack simulations to social engineering and red teaming, our consultants can perform controlled real-world attacks to test your cyber security efforts and assess how your personnel and technology would respond.
Our security experts have years of experience unfolding complex security layers, exposing gaps and vulnerabilities to enhance our client’s security posture.
We understand that all businesses are different, and you may require a specific individualised approach to your requirements.
Our security experts will work with you to achieve your goals and meet your business objectives.
Ensuring the project is delivered on time, within your budget and meets your requirements and expectations.

We are proud of the services that we deliver. Which are continually improved and refined which each assessment, adding value to our clients is what drives us.

Most innovative Cyber Security Startup
We are proud of our highly motivated team who are full of great ideas, that grow our products and services. Adding value to our clients is what drives us.
1-2 Paris Garden, London, SE1 8ND
Hey! Get In touch
We look forward to hearing from you
