By uncovering vulnerabilities and potential security threats, Our cyber security penetration testing services allow you to prioritise and address high-risk areas. This helps reduce the likelihood of a successful attack and mitigate the potential impact of a detrimental security breach.
Prioritise and speed up remediation with point-in-time automated penetration testing. Our testers flag up any key findings as and when they occur so you can resolve weaknesses faster, with our team on hand to provide one-on-one support when you need it.
Our testers fully assess all aspects of your system or network, including hardware, software and people. Using a range of tools and techniques to identify weaknesses, we test various scenarios and attack vectors that an in-house security team may not consider.
Your team has visibility of the entire penetration process from scope to the final report. What's more, assessments can be configured to your specific schedule and frequency. So, you get complete deployment control to suit the requirements of your business..
Detect security vulnerabilities in your network environment, including servers, firewalls and devices.
Secure your online operations and APIs against outside threats and protect sensitive information.
Assess your cloud’s security posture and pinpoint any risks that could leave assets exposed.
Uncover security vulnerabilities and insecure configurations to keep your wireless devices protected.
Get in-depth application assessments to identify weaknesses in your app and keep data secure.
Evaluate and optimise your teams’ security vigilance with social engineering and red teaming.
Tailor our penetration tests to benchmark your organisation's compliance framework, including Cyber Essentials, OWASP, CIS Controls, PCI-DSS, ISO 27001, ISAE3402 and SOC-2.
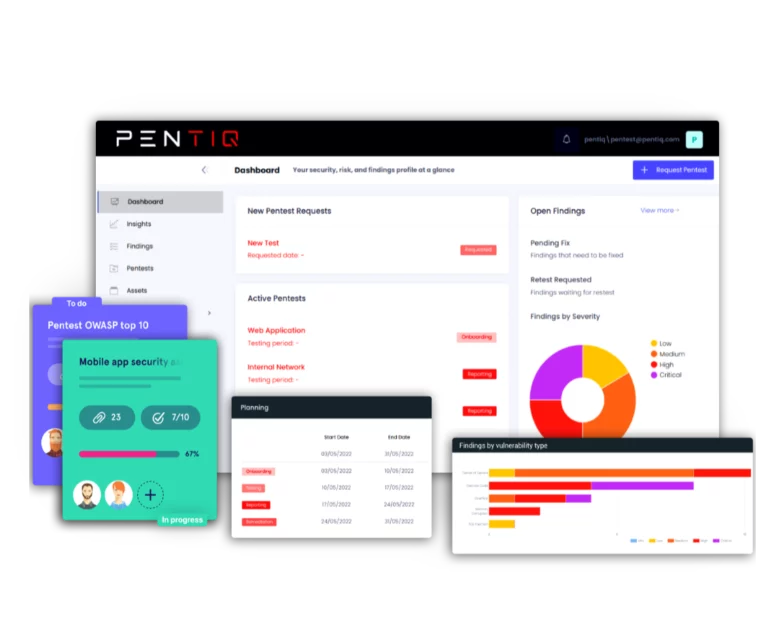
Get point-in-time assessments of your current security posture with activity logs that keep your teams updated with what’s happening and when.
With all your results in one place, your team can address the most critical weaknesses as and when they’re discovered, reducing the risk of hackers exploiting your business.
Assign vulnerabilities to specific users and benefit from workflows, automation and real-time alerts for a complete overview of findings and control to remediate efficiently.
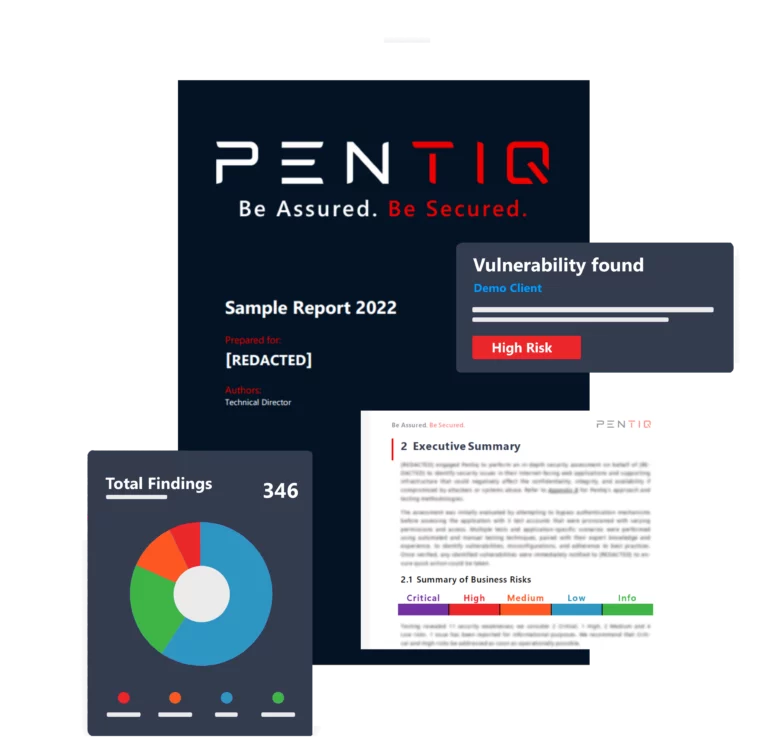
View all your reports, search for specific sections and produce professional reports, which include detailed assessment reviews of any findings and remediations you need to apply.
Easily keep track of any detected vulnerabilities, emerging threats and practical remediation steps for a customisable view of your organisation’s cyber security readiness.
Organise findings by asset, compliance framework, or criticality, to align with compliance, finance, and remediation needs.
Request a PDF report of the current vulnerability status after re-testing fixed findings, so your auditor receives a clean report.
Pentiq delivers cyber security consultancy and penetration testing services to private sector organisations across many industries in the UK, EU, USA & Canada. We use our combined decades of experience across all industries and company sizes – national and global – to provide reliable, cost-effective services tailored to your requirements.
Penetration testing as a service (PTaaS) is a type of security testing that a specialist cyber security company like Pentiq provides as a service. This service is designed to identify vulnerabilities and weaknesses in an organisation’s IT infrastructure, applications and other digital assets that malicious actors could exploit.
REDUCE RISK | INCREASE YOUR SECURITY POSTURE | ACHIEVE CYBER RESILIENCE
A penetration test (pen test) is an authorised simulated attack performed by cyber security and penetration testing experts to discover vulnerabilities that could threaten a business. Organisations can also use a pen test to benchmark compliance with industry standards and frameworks.
During a penetration test, a team of trained security professionals simulates an attack on an organisation’s digital assets. Pentiq testers use the same tools and techniques as attackers to discover vulnerabilities or misconfigurations, attempting to exploit them and providing recommendations to mitigate the identified security risks.
This will depend on your scope and cyber security and penetration testing requirements. A penetration test may be performed externally or internally to simulate different attack vectors.
There are various penetration test types, including network services, applications, client-side, wireless, social engineering, and physical.
Depending on the goals of each test, knowledge shared by a client of the environment and systems to the penetration tester may be given, limited or not provided. These approaches are often referred to as black, grey and white-box.
At least once per year or when there are significant infrastructure changes, this can be driven by compliance, client requests, insurance or M&A.
Those organisations that process substantial volumes of personal and financial data or have strict compliance requirements should conduct testing more often.
Penetration testing aims to provide organisations with a comprehensive view of their security posture, including any gaps or weaknesses that an attacker could exploit. By identifying these vulnerabilities, organisations can take proactive measures to improve their security and reduce the risk of a successful cyberattack.
Our expert security consultants support our PTaaS and deliver interactive reporting and services via our secure portal, helping to provide visibility into your environment. Save time from manual reports and team management, collaborate online, and reduce the time to fix vulnerabilities and exposure to threats by remediating as the testers publish findings.
We deliver our penetration testing and cyber security consultancy services in the UK with our CREST-certified testers located across the country.
Ready to get started?
Get in touch!
We look forward to hearing from you
1-2 Paris Garden, London, SE1 8ND



3-7 Temple Avenue, Temple, London, EC4Y 0DA

Our experts will find your security risks and help you fix them faster. Using our cloud-based portal, you can manage and track findings to reduce cyber threats to your business. Powered by CREST Certified Testers.


3-7 Temple Avenue, Temple, London, EC4Y 0DA
